Cloud Security: Of vs In
Written By: Derek Pocoroba
One of the topics that often comes up when speaking with customers about their challenges is Cloud Security. If you were to ask 5 people, what does cloud security mean to you? You would probably get over a dozen answers, with most of them being right to a degree. Often, we need to take a step back and break this topic down into two fundamental concepts when talking about hybrid and public cloud providers.
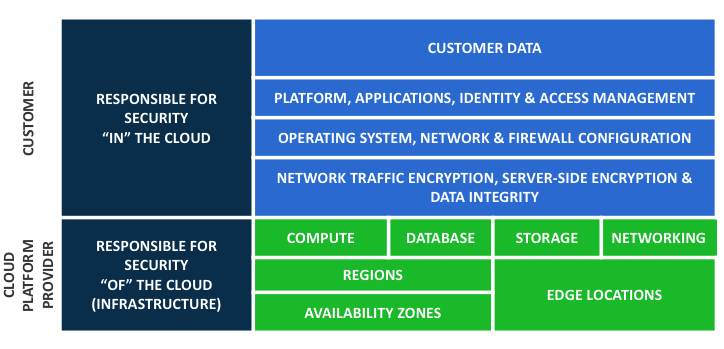
Security OF the cloud VS Security IN the cloud
When you move away from a traditional on-premise data center and towards IaaS (Infrastructure as a Service), Saas (Software as a Service), or other models, you no longer have 100% operational control of the environment. This is known by some cloud providers as the shared responsibility model. In the past, you might have full control of everything from the door locks and fire systems into the data center, to the data stored on the drives. In this new model, control and responsibility are now shared with your provider(‘s), and you have to live by their rules and security.
Security OF the cloud:
What are some things that a cloud provider would have control over? If we take a look at any of the major IaaS providers out there, they will have operation control and responsibility for some of the following:
- Physical hardware/hosts
- Hypervisor layer
- Patching/updates
- Network components
- Access to the facilities
- Regions/Zones
- Software
- SaaS
- PaaS
- Operational access and change control to make foundational changes
As you can see, the cloud providers are responsible for some of the lower-level components and infrastructure of the networks. As we go higher up in the stack the user, you, start to become responsible.
Security IN the cloud:
This is where many people can get themselves into trouble. It is your reasonability to ensure the protection and security of your system that you might deploy using the IaaS examples. For security in the cloud here are some items the end–user becomes responsible for:
- Data
- Encryption rest/transit
- Operating system
- Patching
- Firewalls
- Policies
- Change Management
- Data integrity
There have been plenty of stories of cloud misconfigurations where someone “thought” their data was secure because it was in the cloud. However, if you happen to make that data publicly available to the whole world, and store sensitive data on it, is that the providers‘ fault? The answer is NO; education and understanding of the shared responsibility model are key for developing strong foundational cloud security practices. With new tools and technology, we often need to pause and take a step back. Doing things the way we always have is no longer efficient in a modern cloud–based world.
(Credit cloudcheckr for the image)



Follow Us